Third-Party Code Continues to Expose Users to Risk
Ty Ehuan, Political Science B.A. & Economics B.S., the university of North Carolina at Chapel Hill
The research team at Duke University and the Media Trust continues to track the presence of malicious activity from third-party code as we approach the one-year mark. These incidents are prevalent across the web and this blog post aims to update our readers in what trends we have observed for the month of September. Charts visualizing the areas of note discussed can be found at the bottom of this post. To see previous updates on the status of this project and learn more about the dangers of third-party code please visit our website.
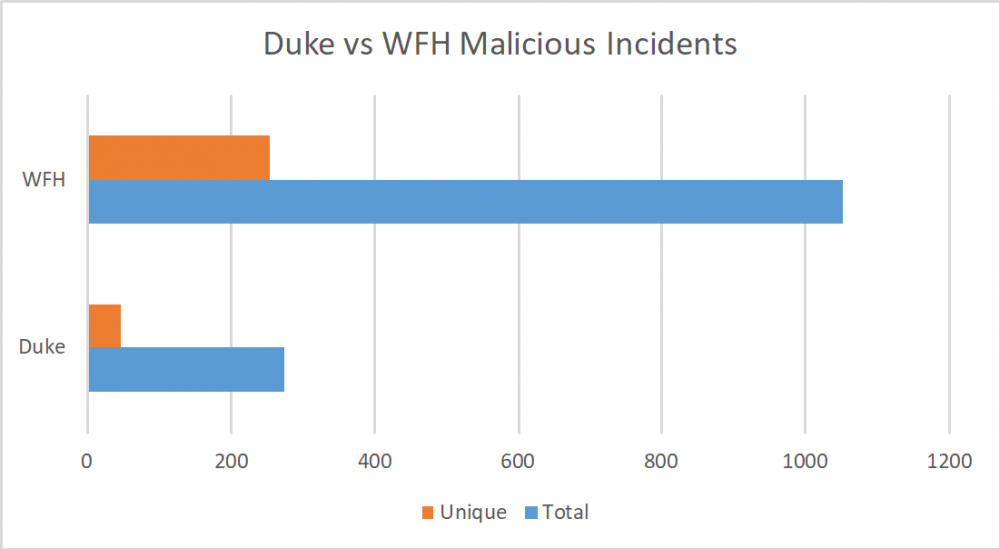
Malicious third-party code remained common in September with .10% and .19% of web interactions with our Duke and Work from Home Profiles respectively resulting in these incidents. Though this number may sound small in isolation, this means these attacks are happening with every 1000 web interactions on average, a number most people can reach in a single day. Thus the majority of people, some of whom have access to critical systems or information, are constantly at risk when they use the internet.
Interestingly the Scan as Duke and Work from Home systems we track have started to diverge more significantly since we last reported our results. After the spike in malware we reported in June, July, and August the relative frequency of attacks has maintained itself for remote worker profiles as their historical average of .13% continues to grow. However, the Duke profiles have seen a significant decrease in percentage of detected attacks returning to their levels at the beginning of the year. This has served to widen the gap between the two, with the Work from Home Profiles now averaging 169% more unique detected attacks since October 2020.
As mentioned in previous reports this trend continues to be primarily driven by one of the two IP’s used on the Work from Home side. This IP has 206% more unique detected attacks than the Duke profiles compared to only 147% for the other IP, a concerning level of increased targeting. The primary factor distinguishing the two is that the heavily targeted IP uses Google Fiber while the other one uses Spectrum. However, this does little to explain the discrepancy between the two as Fiber is generally regarded as having higher security standards than Spectrum. Thus the research team will continue to examine this difference in the hopes of determining why this gap exists and how much of a danger it poses to Fiber users.
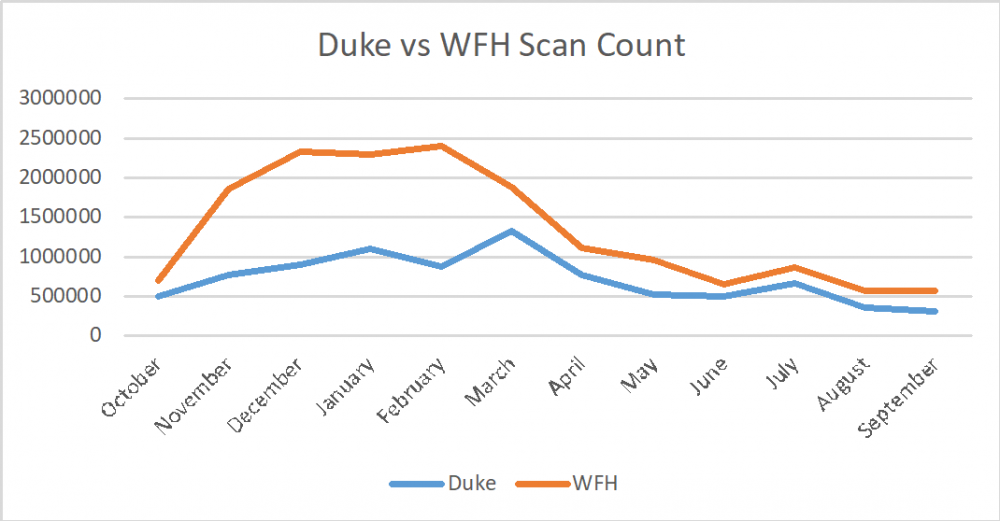
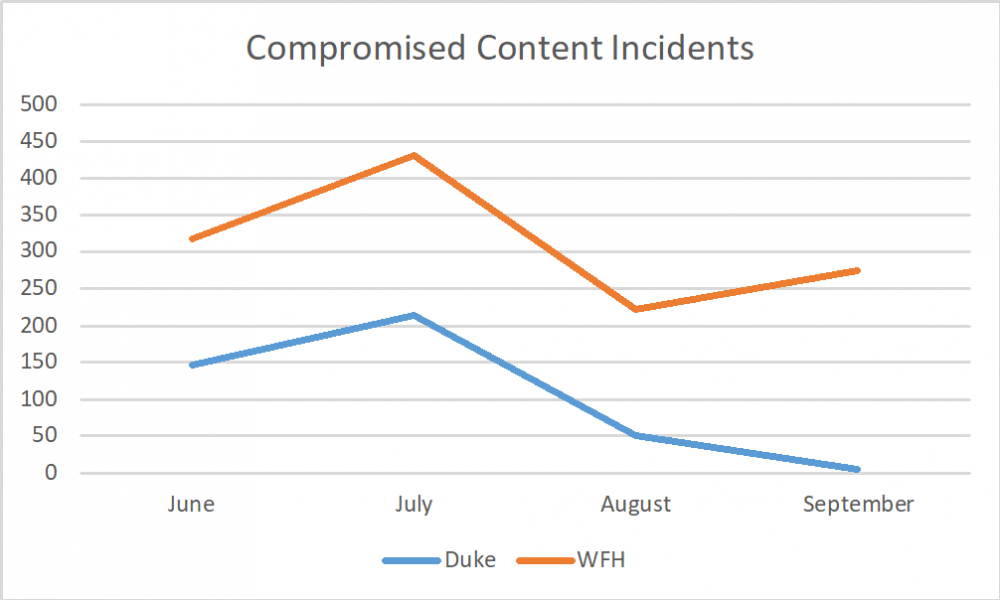
There are two other September trends that bear noting. Firstly, the spike in compromised content attacks found in the last 3 months has disappeared from the Duke profiles while remaining a common attack vector towards remote workers. It remains to be seen whether this is a temporary change or represents a shift in how attackers choose to target different groups. Secondly, the total number of scan counts continues to decline month to month even while the prevalence of attacks remains high. There are still hundreds of thousands of scans being performed each month so this is unlikely to significantly affect the data recorded, but it remains an area to be watched going forward.